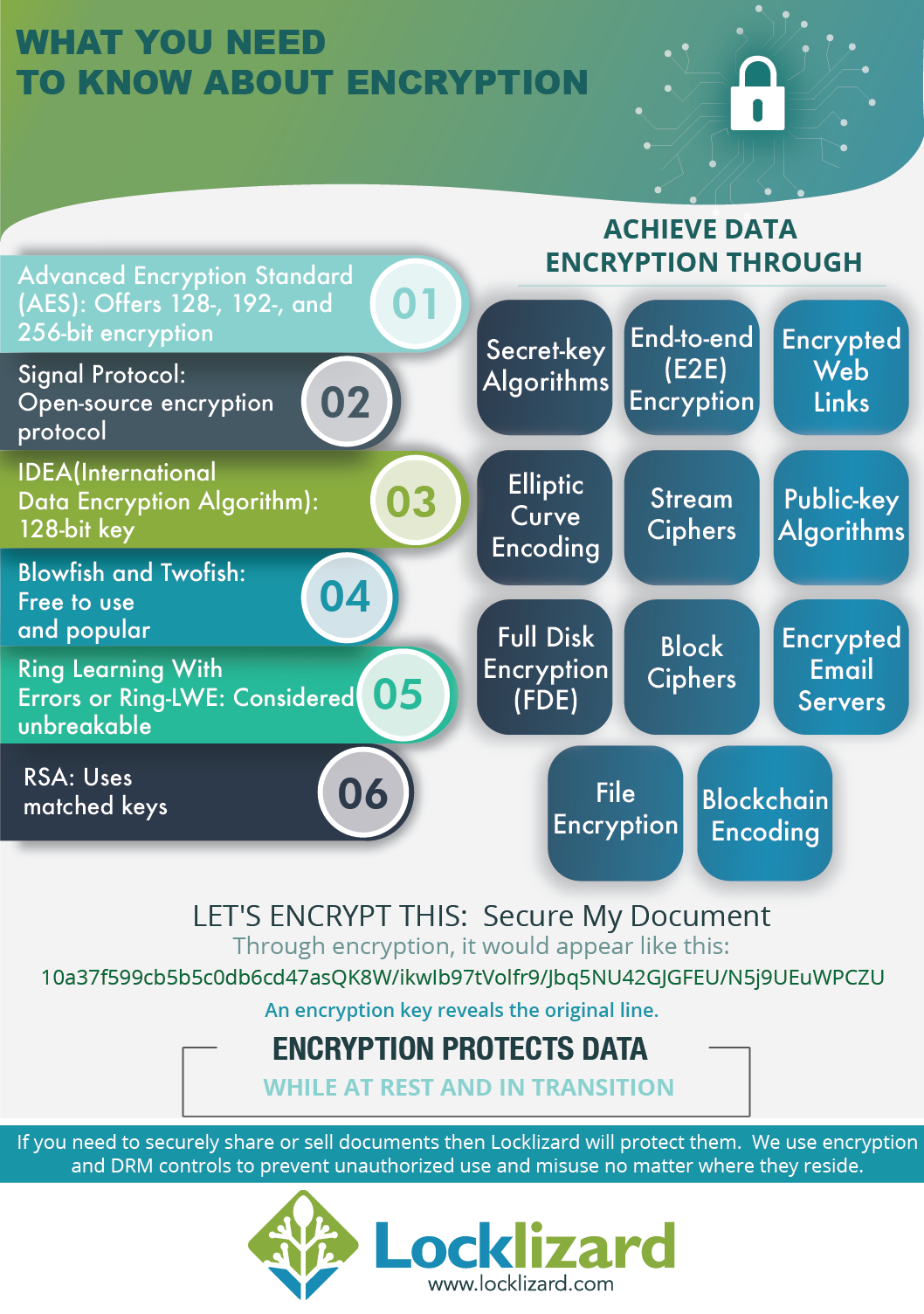
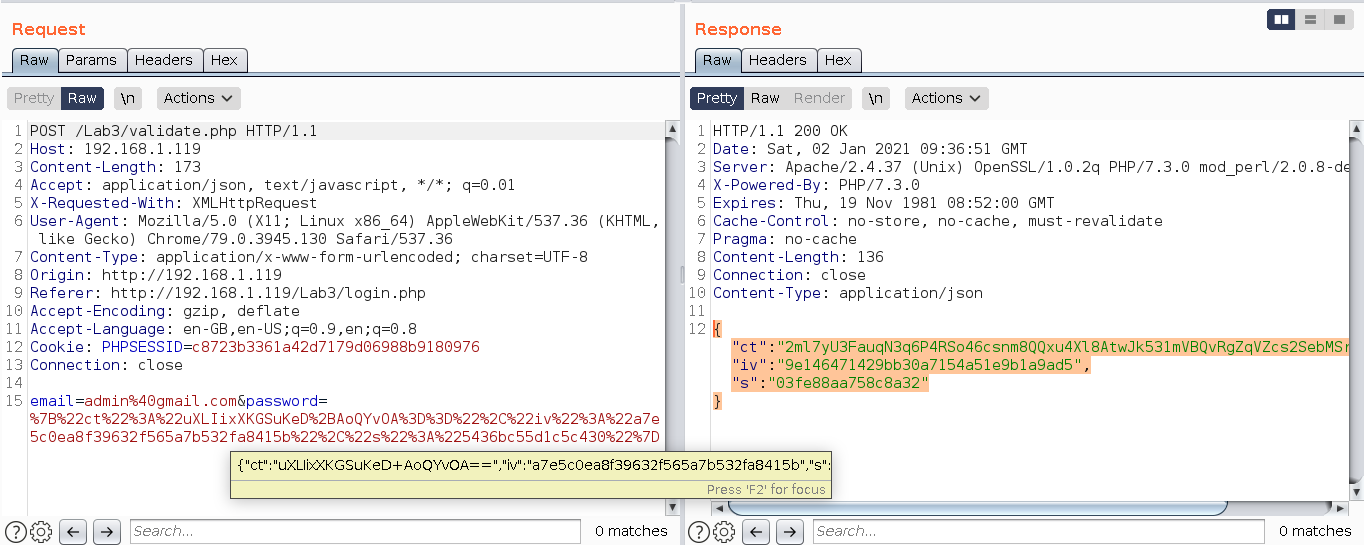
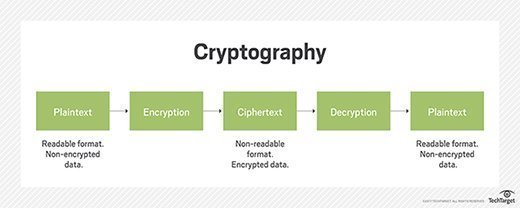
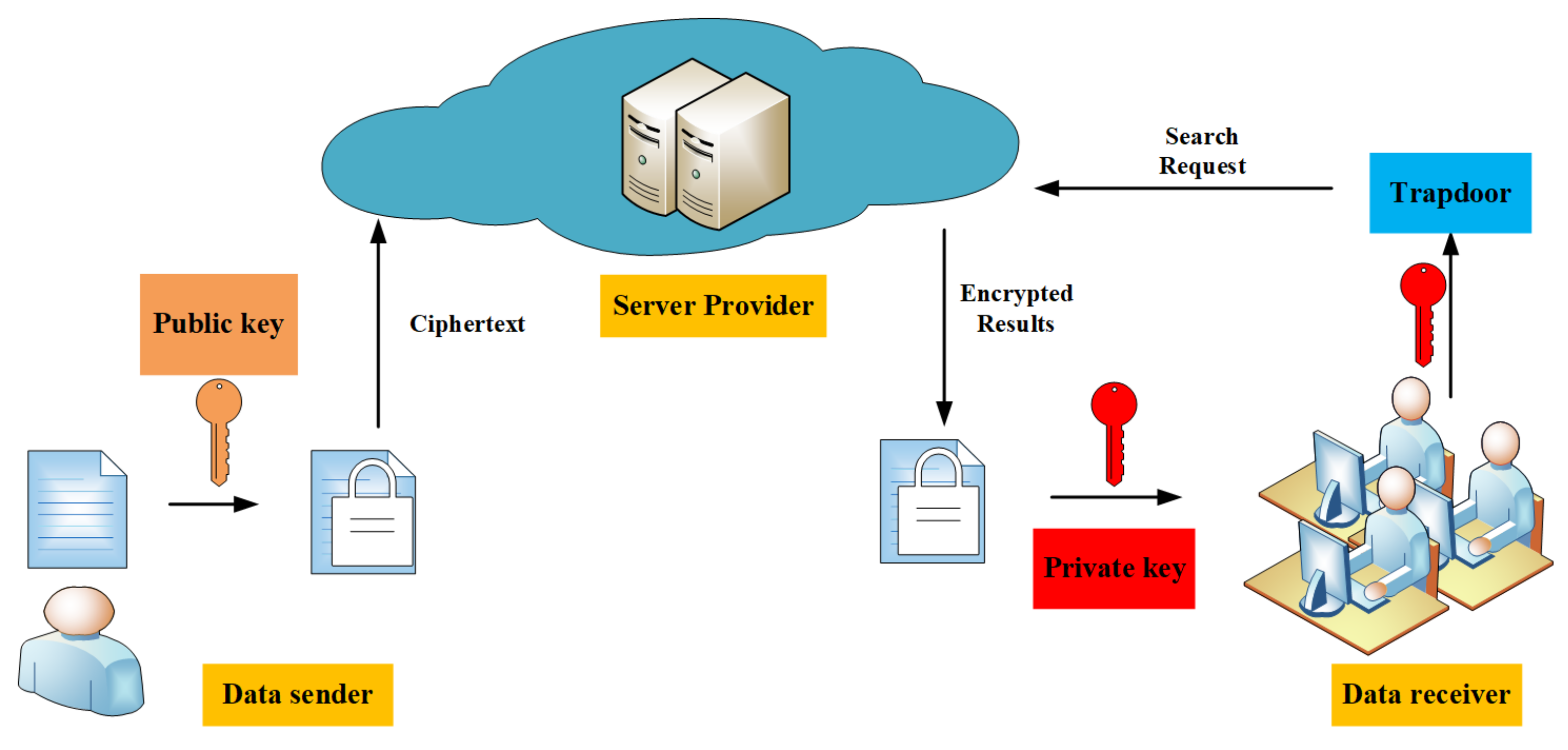
An efficient public-key searchable encryption scheme secure against inside keyword guessing attacks - ScienceDirect
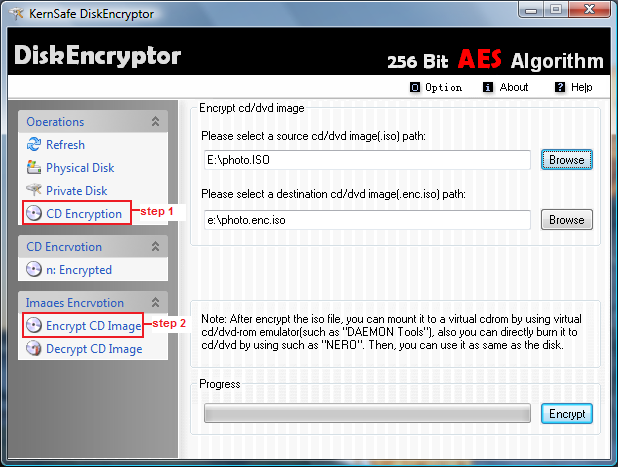
Encrypt CD image This section describes how to encrypt and decrypt a image file. 1. Click Start > Programs >KernSafe> DiskEncryptor>DiskEncryptor; to start up DiskEncryptor; 2. Select CD Encryption under Operations,and then choose Encrypt CD Image ...